You receive an email from your bank. Your account is at risk and you must act immediately. Change your password immediately using the following link. You unsuspectingly click on the link and arrive at a landing page that looks trustworthy. You quickly enter your information and password and change your password instantly. The only problem is that the email was not from your bank, but from a cybercriminal. It was a phishing email.
What is Phishing?
Every day, millions of people click on fake links in emails or app messages designed to steal your password or make you download dangerous malware. You really don’t need to embarrass yourself if it happens to you, because it is often difficult to distinguish a phishing email from a real one.
In phishing, cybercriminals try to trick users into doing “the wrong thing,” such as clicking on a “bad” link that downloads malware, or directing a user to an untrustworthy website. So you can compare it to fishing, because you also entice a fish with fake bait to bite.
Phishing can be carried out via text message, social media or telephone, but the term “phishing” is usually used for attacks that come in via e-mail. Phishing emails can reach millions of users directly and hide among the large number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems or steal intellectual property and money.
How can you recognize a phishing email?
- You will be prompted to click on a link
In a phishing email, the attacker usually wants you to click on a link or open an attachment. But before you click on a link, you better check the email for a few points that we will discuss below.
- The text contains weird spelling mistakes
These days, fake emails have long since ceased to be full of language and spelling errors. Because translation programs like Google Translate or deepl are also getting better and better. Yet sometimes you can tell from grammar, such as crooked sentences, that something is wrong. Unfortunately, the logos and photos used also look increasingly professional. So use your gut feeling.
- The email address is not correct (at all)
Always carefully check the sender’s address. The sender’s name may look exactly like that of your bank or online store, but often the email address used is wrong somewhere. Check the domain name from which you received the e-mail. The domain name can be identified by anything after the @ sign in the email address. If you are not paying close attention you might miss that the letter o in has been replaced by the number 0. An additional tip is to always use a password manager. A password manager will never auto-fill a password on a domain that differs by one letter or number. We recommend Bitwarden.
- Check the link
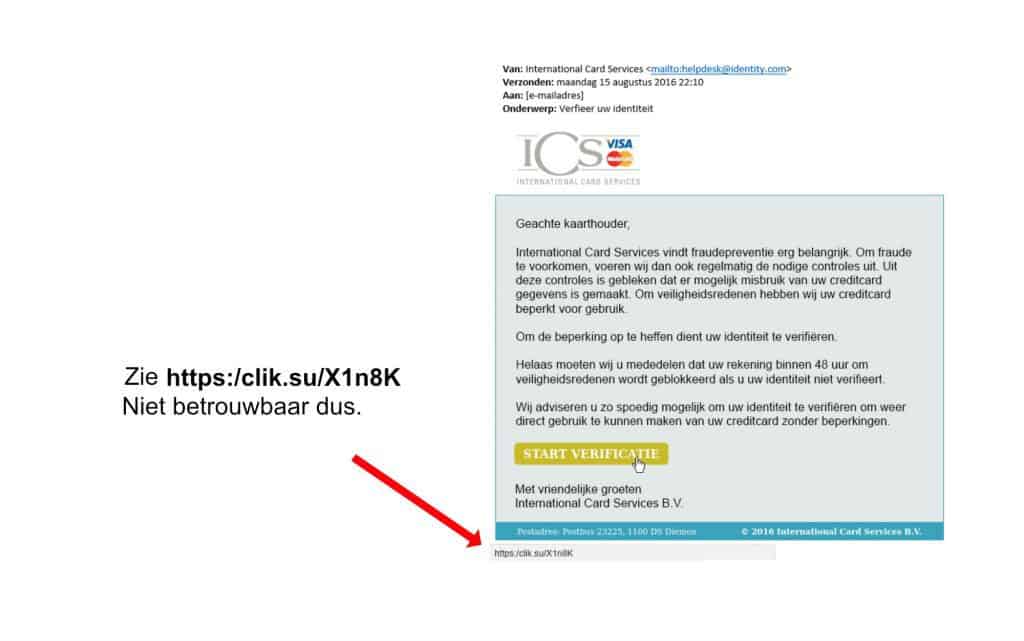
You can often hover over a link (hover over it without clicking!) to see what page you’re directed to. If you don’t trust the link don’t click on it.
- Always watch out when opening attachments
An attachment in a phishing email can cause malicious software to be installed on your computer. So never just open an attachment to an e-mail you don’t trust.
A zip or rar file is always suspicious because, for example, invoices and reminders are never sent this way. But even a pdf file can cause damage to your computer. Still expecting a file? Then contact the sender to ask exactly what and how they sent something.
To do this, never use the contact information in the e-mail (because it belongs to the cybercriminal, but look it up yourself (for example, through the website).
- The email says you must do something immediately, otherwise…
Many phishing emails try to pressure you by using last warnings or urgent notifications. “Your credit card expires, if you do not change your information today your credit card will be blocked.” Do not address this via e-mail, but if in doubt, contact the card issuer by phone.
- Sensitive information is requested
You will usually be asked to verify or complete your personal or payment information. The sender here usually poses as a trusted entity, such as your bank, insurance or the government. Do not click on the link and look for the sender’s contact information yourself to verify authenticity. If you really want to check your information go to the relevant website yourself and log into your account there
Types of Phishing
Clone Phishing
In this attack, criminals create a copy – or clone – of previous delivered and legitimate emails that contain a link or attachment.
The Nigerian prince
A long-winded phishing email from someone claiming to be a Nigerian prince. This is one of the first and longest running scams on the Internet. Often you must first transfer some money to claim an inheritance or fortune.
Spear Phishing
Most phishing emails are sent in bulk to thousands of email addresses in hopes that a few will “bite.” Spear phishing is very targeted and attacks a specific person or organization, often with content that is carefully tailored to the victim or victims. Prior to the attack, reconnaissance work was done to collect names, job titles, e-mail addresses and the like. The cybercriminals scour the Internet to link this information to other data about the target’s colleagues, along with the names and work relationships of key employees in the organization. With this, the phisher constructs a credible e-mail.
Vishing or Phone phishing
In phishing attempts by phone, the cybercriminal calls you and claims to be calling on behalf of your bank, the police or even the IRS. Then they scare you with some problem and urge you to solve it immediately by sharing your account information or else pay a fine. Even with this type of call, it is better to disconnect and call back yourself at a reliable phone number.
Phishing mail examples

A Post NL delivery driver usually lets you know where to pick up a package via a card in the mail, never with an email.

Here you can clearly see that the “click here” link leads to an unreliable domain “condoclima.com”. You should always look at what is before the last .nl or .com.
Always do this to avoid phishing
In almost all cases, it is better to log into a trusted Web site yourself without logging in from an e-mail clicking on a link. If you get an email from your bank to check your information go out of your mail program, open your browser and type in the domain name of your bank yourself that you know is trustworthy. And always use a reliable password manager such as Bitwarden.
